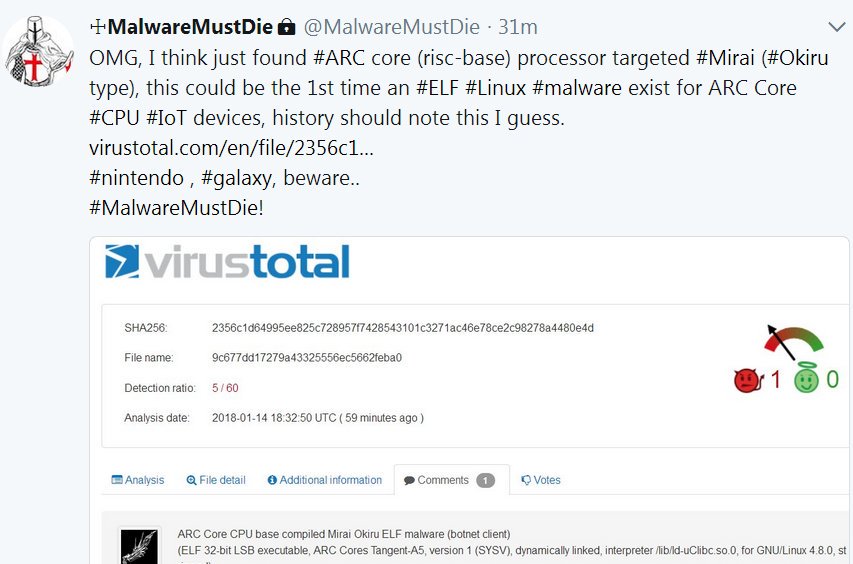
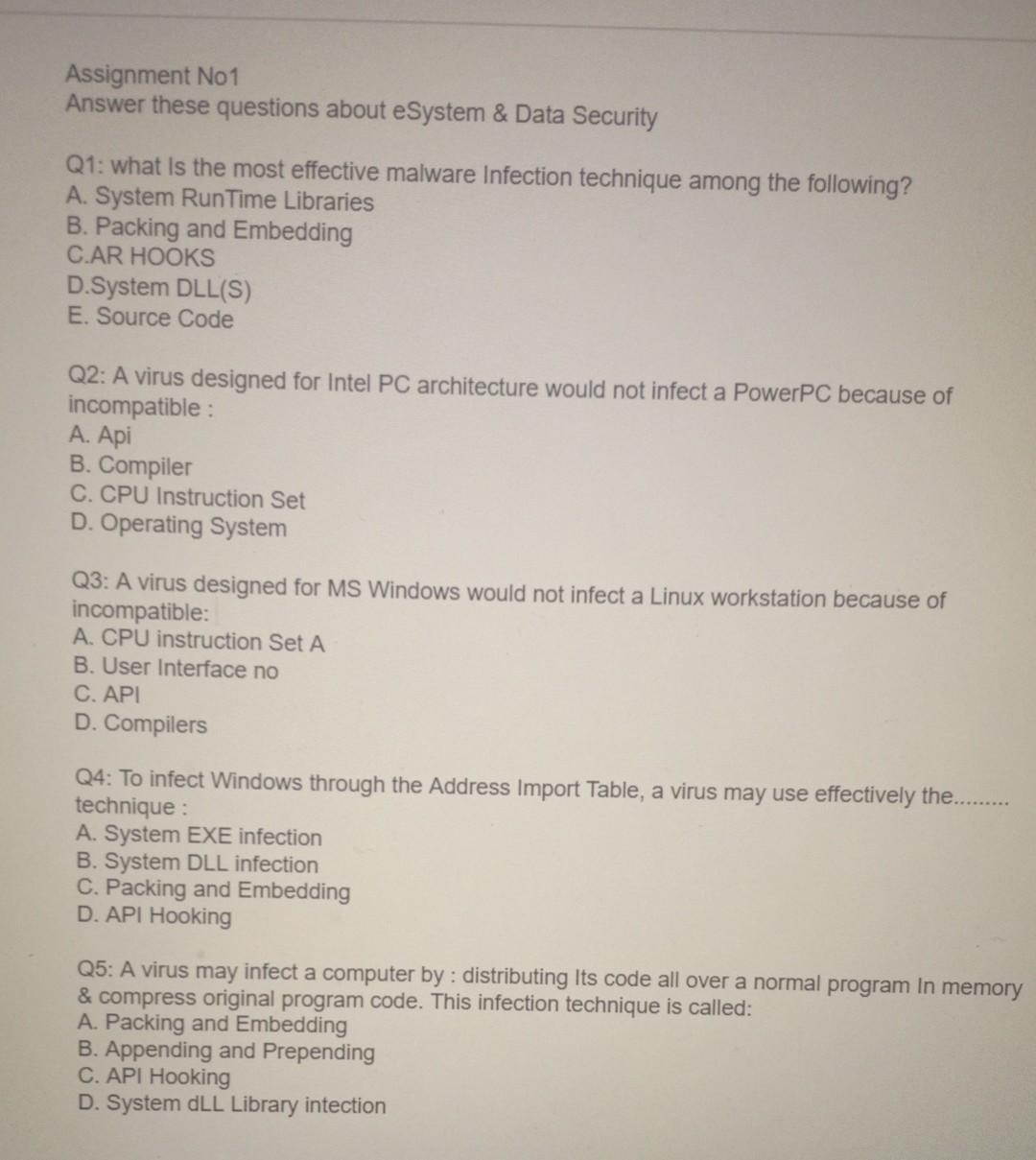
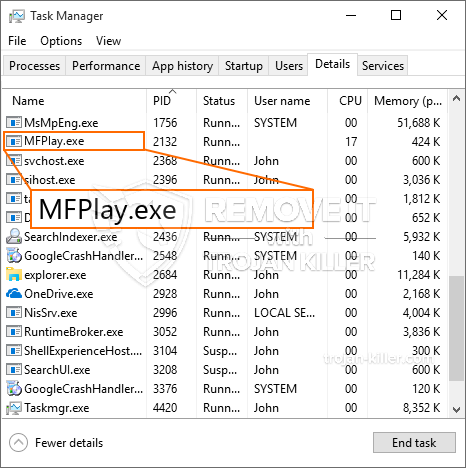
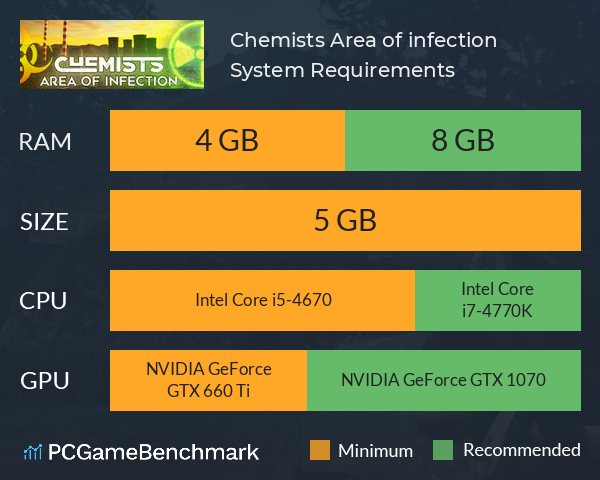
Cyber attack and skull glowing hologram over working cpu in background. Danger alert, threat, infection and warning abstract concept with skull symbol Stock Photo - Alamy

Valnoctamide Inhibits Cytomegalovirus Infection in Developing Brain and Attenuates Neurobehavioral Dysfunctions and Brain Abnormalities | Journal of Neuroscience

Cyber attack and skull glowing hologram over working cpu in background. Danger alert, threat, infection and warning abstract concept with skull symbol Stock Photo - Alamy

PDF) Usefulness and problems of the urinary tract infection criteria for evaluating drug effi cacy for complicated urinary tract infections | Katsumi Shigemura - Academia.edu
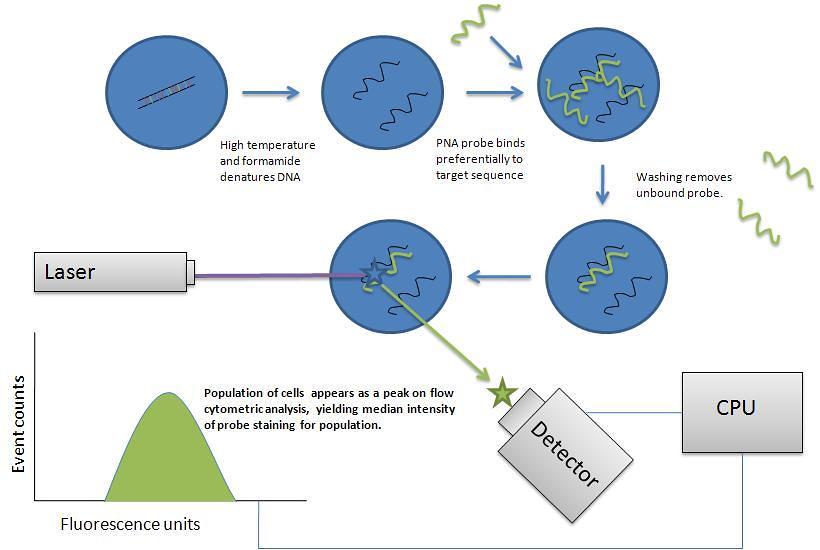
Peripheral blood cell-specific cytokines in persons with untreated HIV infection in Malawi, Africa | Jason and Jarvis Associates, LLC

Cpu On Board With Cyber Attack And Skull Hologram Stock Photo - Download Image Now - Blue, CPU, Computer - iStock

Pichia-secreted mVHH-IgA prevents F4-ETEC infection in piglets a,b,... | Download Scientific Diagram

Cyber attack and skull glowing hologram over working cpu in background. Danger alert, threat, infection and warning abstract concept with skull symbol Stock Photo - Alamy